Authenticating to the Power Platform is not always possible via username and password, especially not if MFA is activated. It’s not secure if you allow connections with only a username and password.
In such cases, you can connect using a service principal (app registration).
Creating a new management application
First, you need to create a new app registration in Azure Active Directory to connect to the Power Platform. In this article we will not focus on this part.
After your app registration is created, you need to “register” it in the Power Platform. This cannot be done via the UI of the Power Platform Admin Center. You can do this with PowerShell.
The application needs to be registered by a user who has the Power Platform Administrator role.
$appId = "CLIENT_ID_FROM_AZURE_APP"
# Login with a Power Platform Administrator user
Add-PowerAppsAccount -Endpoint prod -TenantID $tenantId
# Register new application
New-PowerAppManagementApp -ApplicationId $appId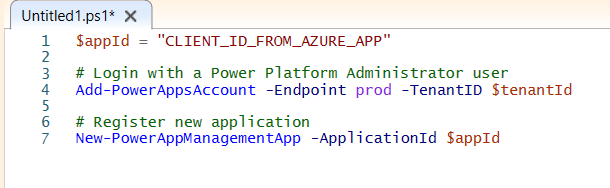
Execute commands in the name of a service principal
After creating your management application, you can authenticate to the Power Platform with the service principal.
$appId = "CLIENT_ID"
$secret = "SECRET"
$tenantId = "TENANT_ID"
Add-PowerAppsAccount -Endpoint prod -TenantID $tenantId -ApplicationId $appId -ClientSecret $secret -Verbose
Get-AdminPowerAppEnvironment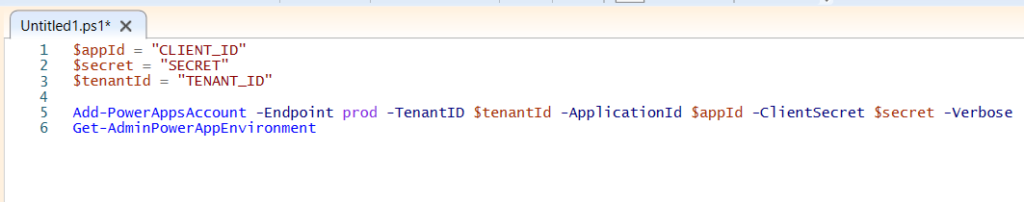
Azure Automation and Runbooks
Power Platform Administrators can create a Runbook in Azure Automation. This allows to run administrator related PowerShell scripts. Some use cases:
- Scheduled script to remove shares of flows in the default environment
- Scheduled script to make a list of assigned DLP policies grouped by environment
A service principal or app registration can be used to connect to the Power Platform from a PowerShell script that runs in a Runbook.